Nearly 10 Billion Passwords Leaked Online: Top 5 Cybersecurity Growth Stocks To Watch
Largest Data Breach in History: Nearly 10 Billion Passwords Leaked Online
Disclaimer: The information presented in this article is based on current knowledge and research at the time of writing. The situation may evolve as new data becomes available. Readers are encouraged to stay informed and take appropriate measures to protect their personal and organizational data.
Real-time information is available daily at https://stockregion.net
On July 4, 2024, a massive cybersecurity incident unfolded that has been dubbed the largest data breach in history. A user, known by the handle "ObamaCare," posted a file named rockyou2024.txt on a hacker forum. This colossal file contains a staggering 9,948,575,739 unique passwords, making it one of the most extensive collections of leaked passwords ever discovered.
The rockyou2024.txt file is a compilation of passwords gathered from over 4,000 database breaches spanning the past two decades. These breaches have collectively contributed to the near 10 billion unique plaintext passwords now available for malicious purposes. This unprecedented cache of passwords poses a severe security threat to individuals, corporations, and various types of internet-connected devices. The name "RockYou" may sound familiar to those well-versed in cybersecurity history. It harkens back to a previous breach in 2009 involving the social application developer RockYou, wherein millions of user accounts were compromised. The rockyou2024.txt file can be seen as a modern-day escalation of similar incidents, but on an exponentially larger scale.
Cybernews researchers emphasize that the rockyou2024.txt compilation effectively heightens the risk of credential-stuffing attacks. Credential stuffing is a cyberattack technique where attackers use automated tools to input large volumes of username and password combinations until they gain unauthorized access to user accounts. The passwords included in the rockyou2024.txt file originate from numerous breaches across various sectors, including retail, healthcare, finance, and more. Since 2021 alone, around 1.5 billion passwords have been added to this colossal database, reflecting an alarming increase in the frequency and scale of data breaches.
Brute force attacks represent one of the primary methods by which these stolen passwords can be exploited. In a brute force attack, an attacker systematically attempts all possible passwords until the correct one is found. With the vast dataset provided in rockyou2024.txt, hackers can automate this process, testing millions of passwords with relative ease. Systems not adequately protected against brute force attacks could be quickly compromised using this database. The compilation of such a vast number of real-world passwords offers insights into common password patterns and behaviors, which further aids attackers in refining their brute-force strategies.
Credential Stuffing and Broader Risks
Credential stuffing takes advantage of the fact that many users reuse passwords across multiple accounts. By using known credentials from one breach, attackers can potentially gain access to additional accounts. This is particularly concerning for organizations and services that rely on password-based authentication for security. Researchers warn that both online and offline services are at risk. This includes internet-facing cameras, industrial hardware, and other connected devices. The consequences of such breaches can range from unauthorized surveillance to disruptions in critical infrastructure. When combined with other leaked datasets containing user email addresses and other credentials, the rockyou2024.txt file can precipitate a cascade of data breaches. Financial fraud, identity theft, and other forms of cybercrime become easier to perpetrate with such comprehensive information.
Given the enormity of this breach, it is essential for both individuals and organizations to adopt robust security practices to mitigate potential threats. Here are recommended strategies:
Use Strong, Unique Passwords: Ensure that each account has a strong, unique password that combines letters, numbers, and special characters.
Enable Multi-Factor Authentication (MFA): MFA adds an additional layer of security by requiring a second form of verification, making it harder for attackers to gain access even if they have the password.
Regularly Update Passwords: Change passwords periodically to limit the potential damage from older breaches.
Employ Security Tools
Password Managers: Use password managers to generate and store complex passwords securely.
Leaked Password Checkers: Utilize tools like the Leaked Password Checker to verify whether your credentials have been compromised.
Monitor and Respond
Monitor Accounts for Unusual Activity: Regularly check for any suspicious activity on your accounts and take immediate action if any anomalies are detected.
Educate Users: Organizations should educate employees and users about the risks associated with reused or weak passwords and encourage best practices in password management.
Implement Advanced Security Measures
Intrusion Detection Systems (IDS): Deploy IDS to monitor network traffic for potential signs of an attack.
Rate Limiting: Implement rate limiting to reduce the effectiveness of automated attacks by restricting the number of login attempts within a specified period.
Behavioral Analytics: Use behavioral analytics to detect unusual login patterns that may indicate a credential stuffing attempt.
The rockyou2024.txt file represents an unprecedented challenge in the realm of cybersecurity. Nearly 10 billion unique passwords are now in the hands of threat actors, increasing the risk of widespread cyberattacks. There's an urgent need for enhanced security practices and vigilance among individuals and organizations alike. By understanding the scope and implications of this breach and adopting proactive security measures, we can better protect our digital lives and assets from malicious actors.
5 American Growth Cybersecurity Stocks to Watch
Amidst the news of the largest data breach in history, where nearly 10 billion passwords were leaked online, the cybersecurity sector is likely to gain attention. Investors may look to cybersecurity companies that are poised for growth as they provide vital solutions to combat such threats. Here are five American growth cybersecurity stocks to watch:
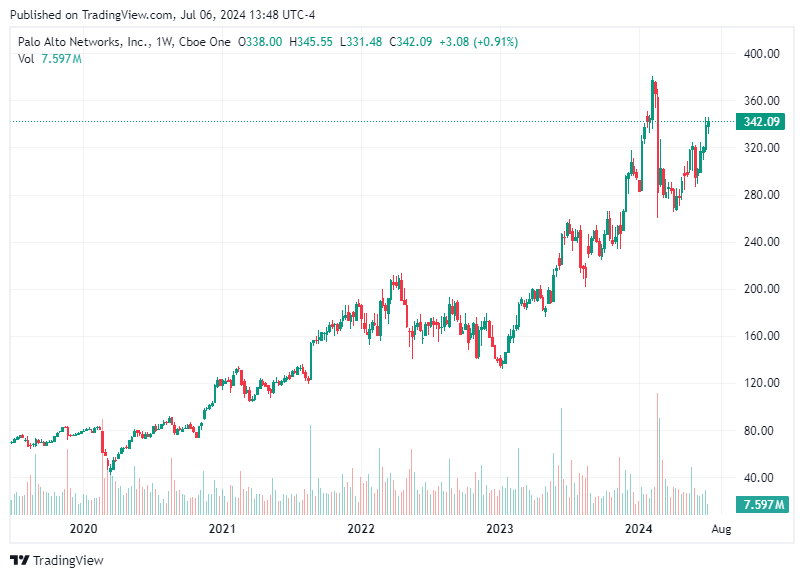
1. CrowdStrike Holdings, Inc. (CRWD)
CrowdStrike is a leading provider of cloud-delivered endpoint protection. The company's Falcon platform leverages artificial intelligence (AI) and machine learning to detect and prevent breaches in real-time. CrowdStrike has been consistently growing its revenue and customer base, making it a strong contender in the cybersecurity market.
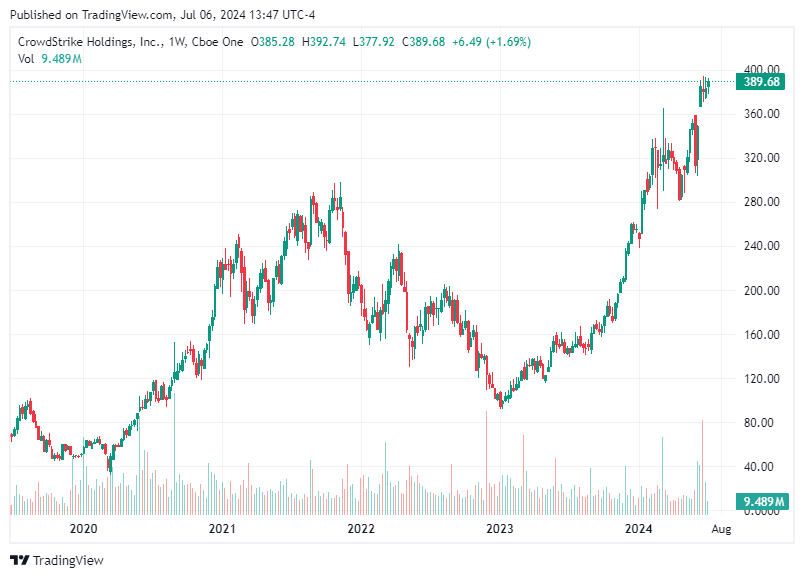
2. Palo Alto Networks, Inc. (PANW)
Palo Alto Networks offers a wide range of cybersecurity services, including advanced firewalls, threat intelligence, and cloud security solutions. The company has been expanding its portfolio through acquisitions and innovations, positioning itself as a comprehensive cybersecurity provider.
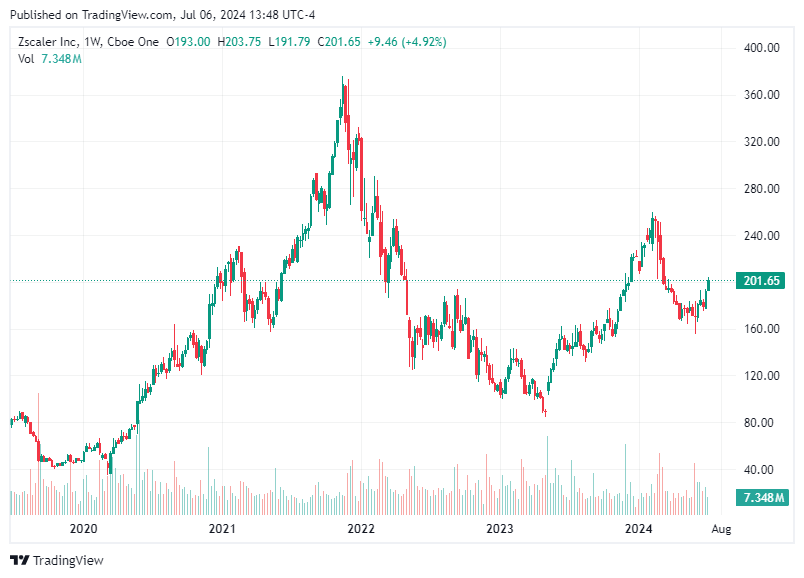
3. Zscaler, Inc. (ZS)
Zscaler specializes in cloud-based internet security and provides secure access to applications and data. With the increasing shift towards remote work and cloud adoption, Zscaler's zero-trust security model is becoming increasingly relevant. The company has shown strong revenue growth and continues to expand its service offerings.
4. Fortinet, Inc. (FTNT)
Fortinet is known for its high-performance network security solutions, including firewalls, intrusion prevention systems, and endpoint security. The company's Security Fabric architecture integrates its various products, providing a unified approach to cybersecurity. Fortinet has a robust financial performance and a broad customer base.
5. Okta, Inc. (OKTA)
Okta provides identity and access management solutions, which are crucial for securing user identities and managing permissions. Okta's platform enables secure connections between people and technologies, ensuring that only authorized users can access sensitive information. The company's growth is driven by the increasing need for identity security in a digital world.
Newly Listed American Growth Cybersecurity Stocks
In addition to established players, there are also newly listed cybersecurity companies that have recently entered the market and show potential for growth. Here are a few newly listed American growth cybersecurity stocks:
1. SentinelOne, Inc. (S)
SentinelOne is a cybersecurity company that provides endpoint protection solutions powered by AI. The company's Singularity platform offers autonomous threat detection, prevention, and response capabilities. SentinelOne went public in June 2021 and has since been gaining traction in the market.
2. Darktrace plc (DARK)
Although Darktrace is a British-American company, its presence in the U.S. market is significant. Darktrace specializes in AI-driven cybersecurity solutions that detect and respond to threats in real-time. The company went public in April 2021 and has been expanding its reach and capabilities.
3. ForgeRock, Inc. (FORG)
ForgeRock provides identity and access management solutions, focusing on enterprises' digital identity needs. The company's Identity Platform helps organizations securely manage identities across various environments. ForgeRock went public in September 2021 and is well-positioned to benefit from the growing demand for identity security.
4. KnowBe4, Inc. (KNBE)
KnowBe4 offers security awareness training and simulated phishing platforms to help organizations educate employees about cybersecurity threats. The company's unique approach to improving human defense against cyberattacks has gained popularity. KnowBe4 went public in April 2021.
5. Riskified Ltd. (RSKD)
Riskified is an e-commerce fraud prevention company that leverages machine learning to protect online merchants from fraud. The company's platform helps businesses approve legitimate transactions while blocking fraudulent ones. Riskified went public in July 2021 and is expanding its market reach.
The recent massive data breach highlights the critical importance of robust cybersecurity measures. Investors looking to capitalize on the growing demand for cybersecurity solutions may consider both established and newly listed cybersecurity stocks. Companies like CrowdStrike, Palo Alto Networks, Zscaler, Fortinet, and Okta offer proven growth potential, while newer entrants like SentinelOne, Darktrace, ForgeRock, KnowBe4, and Riskified present emerging opportunities in the dynamic cybersecurity landscape. As the threat landscape evolves, these companies are well-positioned to provide essential solutions to protect against cyber threats.
Disclaimer: The details and recommendations provided in this article are based on current information and research. Readers are advised to stay updated with the latest cybersecurity developments and practices to ensure ongoing protection.
Real-time information is available daily at https://stockregion.net


